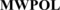Mobile Device Management (MDM)
Mobile Device Management (MDM) is a software solution that enables organizations to effectively manage and secure mobile devices used by employees. MDM is designed to give IT departments a way to monitor and control mobile devices, such as smartphones and tablets, that are used to access corporate data and applications.
One of the key features of MDM is the ability to create and enforce security policies on mobile devices. This includes setting up password complexity requirements, enabling encryption, and setting up remote wipe capabilities. This ensures that if a device is lost or stolen, sensitive data can be wiped from the device to prevent it from falling into the wrong hands.
Another important aspect of MDM is the ability to monitor and track mobile devices. This includes the ability to locate a device on a map, view device usage statistics, and track the device's battery level. This helps IT departments to keep track of their devices and troubleshoot any issues that arise.
MDM also allows organizations to deploy and manage mobile apps. This includes the ability to distribute apps to devices, as well as to manage updates and upgrades. This can help organizations to ensure that employees have access to the apps they need to perform their work, while also maintaining control over the apps that are installed on devices.
In addition, MDM can help organizations to comply with industry regulations. For example, healthcare organizations must comply with HIPAA regulations, which require that certain security measures are in place to protect patient data. MDM can help these organizations to meet these regulations by enforcing security policies and monitoring mobile devices.
In summary, Mobile Device Management (MDM) is a software solution that allows organizations to secure, monitor, manage, and support mobile devices used by employees, ensuring the safety and security of sensitive data and compliance with industry regulations. It is an essential tool for businesses to protect sensitive data, maintain compliance, and keep track of mobile devices.
The terms UEM, MDM, and EMM are often used interchangeably by some individuals.
MDM Implementation
Implementing an MDM solution in a business environment requires proper planning and dedication. The software streamlines device setup and provisioning, including bulk loading of applications and configurations, as well as ongoing updates and maintenance. To ensure a successful deployment, it is advisable to implement the MDM software at the time of purchasing new devices. Businesses should choose an MDM vendor that can cater to their specific requirements and supports their business needs. In the US, smartphones and tablets are commonly sold through mobile carriers, who work with various MDM software providers. It's crucial for businesses to choose a robust and reliable MDM vendor that aligns with their needs. The device platform also plays a crucial role in choosing the right MDM solution. For instance, some platforms may have specific capabilities or limitations that the business needs to consider. In conclusion, businesses should consider both the device platform and MDM vendor when selecting an MDM solution to ensure they meet their business requirements and goals.
Difference between Android and iOS MDM
Android phones and tablets now come equipped with the Android Enterprise framework, which offers comprehensive enterprise mobility management APIs and prioritizes data leakage prevention (DLP). During device provisioning, the MDM software transforms the consumer Android device into a business-ready device.
Apple devices can be provisioned with Mobile Device Management (MDM) software through the Apple Business Manager (ABM) portal. The ABM portal verifies device ownership and offers complete remote management capabilities. To use ABM, organizations must sign up on the portal, purchase iPhones or iPads and wait for about a week for the ABM organization ID to be activated. Devices purchased through ABM are shipped ready for MDM zero-touch enrollment and are fully configurable remotely in a supervised state. For legacy iOS devices, they must be assigned to ABM through the Apple Configurator app on a MacOS computer. However, as of iOS 16, the app is also available on iPhones.
The ABM process allows for over-the-air MDM profile installation without the need for physical device access. Once the device is powered on and connected to a Wi-Fi or cellular network, it automatically connects to the ABM server and downloads and installs the MDM profile. The end user cannot disable or prevent the MDM installation. This process is similar to the Android Zero Touch enrollment or KNOX mobile enrollment for Samsung devices. Typically, an MDM will block a soft factory reset, but will still be reinstalled on the device even after a hard factory reset.
iOS devices are provisioned with MDM software by installing an MDM profile (plist XML file), which communicates with the MDM server through the built-in iOS MDM client to enforce policies. In contrast, Android devices typically require the installation of an MDM app, which communicates with the MDM server to receive and enforce configurations on the device.
Understanding available provisioning methods
| Company Owned | Android Enterprise QR code | Factory reset is required, enabling full management |
| Android Zero Touch | Factory reset is required, enabling full management | |
| KNOX Mobile Enrollment (KME) | Factory reset is required, enabling full management | |
| Apple Business Manager (ABM) | Factory reset is required, enabling supervision and full management | |
| Apple Configurator | Factory reset is required, assigning the device to ABM and enabling supervision and full management | |
| BYOD | Android App (APK) based Enrollment | Creates a workspace container in the Android Device. In the BYOD scenario, device control is more limited. |
| iOS Profile Install through Safari | Installs an MDM profile in the device for BYOD providing limited controls. |
Understanding Different Provisioning Profiles in Enterprise Mobility Management
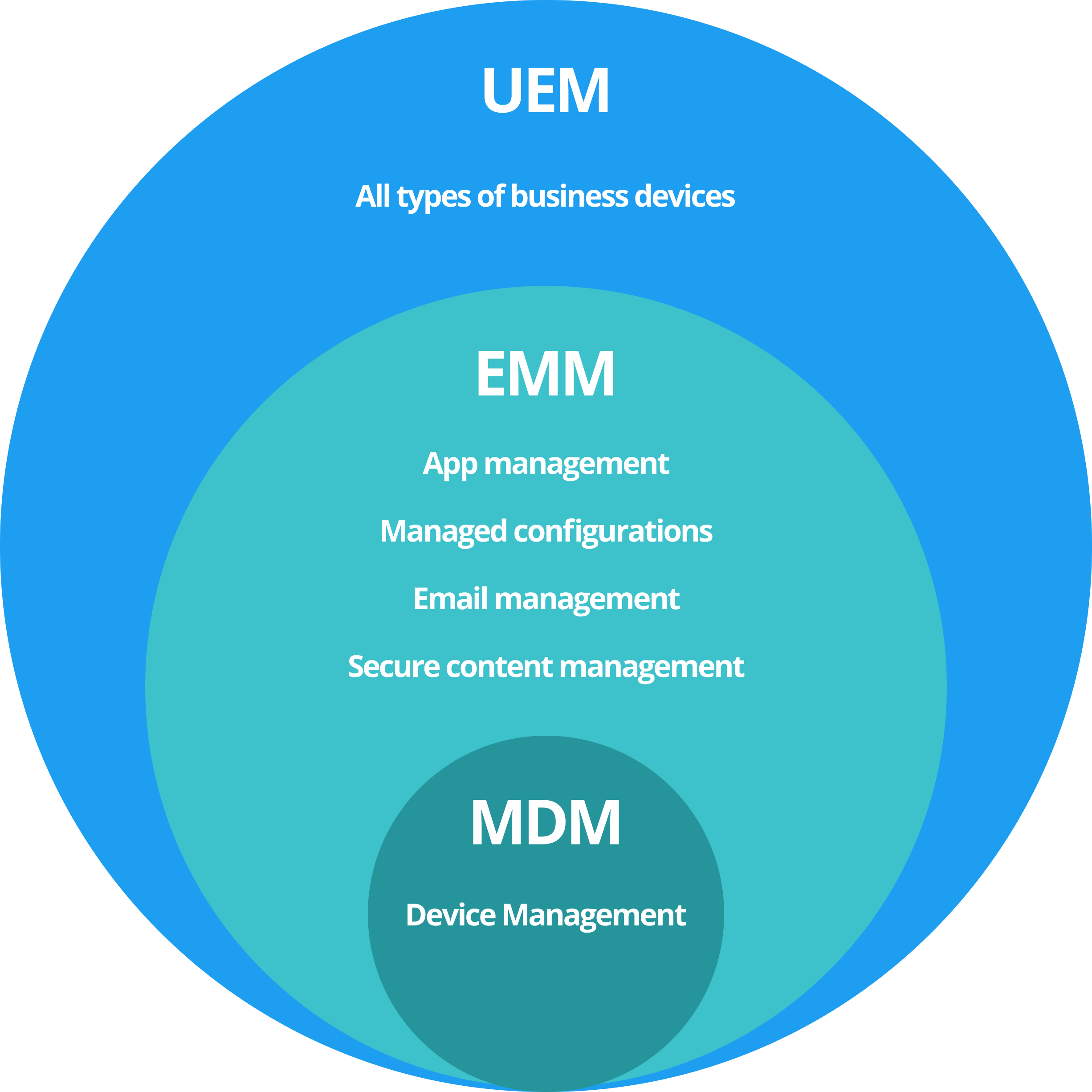
Company Owned, Personally Enabled (COPE): In this scenario, company-owned devices are issued to employees for both personal and work use. The device is fully managed by the company's IT administrator, but employees can use their personal Gmail or Apple iTunes accounts to download public apps. They can also keep personal contacts and photos in the primary device profile. Some MDM solutions allow for a separate work profile container on the device to house and manage business apps. The device is trackable and can be remotely wiped by the IT administrator, and the end-user cannot disable MDM control.
Company Owned, Fully Managed: Devices in this category are used solely for work purposes and all apps are managed and updated by the IT administrator. End-users can only install enterprise-approved apps and cannot download external apps. Pre-loaded apps are blocked during provisioning, and the home screen has a company-specified wallpaper or logo. The Settings app is enabled but with limited capabilities, and the end-user cannot remove the apps or disable MDM control.
Company Owned, Kiosk Enabled: Devices in this configuration are highly restricted, with only whitelisted apps available, and buttons and notifications blocked. All OEM pre-loaded apps are erased, making it ideal for use in retail, hospitality, digital signage, and other industries. On Android devices, this requires enabling lock task mode or using a custom home launcher app. On iOS devices, single app mode can be enabled through MDM, running in full-screen mode and potentially restricting touch control, buttons, speakers, camera, and microphones. If multiple app support is needed, it's recommended to use iOS restrictions to whitelist and blacklist apps on a supervised device.
Employee-Owned (BYOD): In the case of Android devices, there are two profiles: a primary profile for the user's personal information and apps, and a temporary workspace container created during enrollment for work-related apps and contacts. The IT administrator only has control over the workspace container and can enforce password requirements and wipe its contents, but has no control over the device's camera, settings, or accounts. Typically, the end-user installs the MDM app from the Play Store or as an APK package from an internal website, and the MDM app then creates the container and sets up the necessary profile. For iOS devices, there is no separate container, but instead, the MDM profile is installed and managed through the Settings app. The end-user can remove the MDM profile at any time from the Settings app. In both platforms, the enrollment process does not require a factory reset of the devices.
When selecting an MDM solution, it's important to consider the different provisioning profiles offered. These profiles determine the level of control and access to device features that can be exercised by the IT administrator. For example, a manager's profile might have a less restricted configuration compared to field employees who use the device for a specific purpose.
It's crucial to choose an MDM software that offers the provisioning methods and management features required by your organization. Switching from one MDM to another can be difficult, especially if thousands of devices have already been enrolled with the initial solution. To ensure you make the best decision, it's recommended to test each MDM with a few devices before making a final purchase.
"Throughout my experience with Codeproof, it has worked flawlessly. Even more importantly, Codeproof support is unrivaled."
Working with Codeproof has been a relief, it allows our company to have control over software and devices and visibility to ensure our employees have the proper equipment to do their job each and every day.
We didn’t make a single compromise to get the protection we wanted and needed.
We have site phones that we need locked and tracked. We have recovered lost or stolen phones...and pushed new apps remotely.
The Codeproof platform not only assists in fleet management, but has benefitted our company in helping to make the process of retrieving company property more reliable.
Customer support is always accessible and those who have assisted us have gone out of their way to ensure the MDM platform meets all of our needs.
Codeproof had the right balance of easy individual device configuration and group-level settings, as well as an excellent support team and willingness to add new features to meet our needs, all at a competitive price.
Having our employees work in remote locations, Codeproof has really helped us manage our devices...They are very helpful and detailed when explaining thing.
Codeproof has made device management much easier than some larger MDM solutions. From the beginning of our trial Console, up to the present, we were able to easily contact the development team at Codeproof with any ideas for improvements.
With Codeproof, the first thing I noticed is that the UI is much more intuitive and simpler to navigate. I feel like there are as many, if not more, features available to me in Code Proof but they are a little easier to find.
Foundation is so grateful for the partnership with Codeproof and their willingness to support students and families in need of literacy resources. While our technical needs are likely less than that of other companies, we have found great value in the Codeproof product.
Codeproof has great customer support. If there is an issue, or if we need assistance with anything, they are very quick to respond and lend a hand.
Terrapin Pharmacy’s Executive Management and Technology Developers would be extremely likely to recommend Codeproof to others based upon the interactions we have had with the Codeproof team and the can-do culture within their organization.
Codeproof is a very comprehensive MDM product. We received great service at all times from their technicians when we had issues. They are continually working on improving the product with feedback from customers like us, so we can have better control of our remote equipment.
[An] upbeat, well-organized, and helpful company. Codeproof provided superior customer support during a time of uncertainty.
Codeproof has been an asset in maintaining security, control and reducing liability of our mobile devices by allowing us blanketed control of our mobile fleet at all times regardless of day and location. It will continue to be the foundation for our mobile security for now and the future. Their security options and scalability is priceless.
I chose Codeproof over other players in the market because it's simple and customizable dashboard caters to the needs of my business. Codeproof tries to find solutions and treats you as partners rather than just a customer.
I chose Codeproof for our internal MDM solutions over other options because the case study and utilization of the system were very understandable. It decreased our potential costs related to device investments while increasing device security and reducing operational costs.
















 Hotline: 1-866-986-BYOD
Hotline: 1-866-986-BYOD